Why trust is the deciding factor in whether I attend your conference
Do I trust you?

I live in rural Vermont, so if I want to go to an in-person conference that isn’t close to me, I need to get on an airplane.
The closest airport to me is a two-hour drive. Unless the event is in the northeastern United States, I need a full day to get there and another to return, even longer if it’s abroad.
For me—and, I suspect, most attendees—getting there is one factor in choosing whether to attend. But it’s only one factor. As Seth Godin says:
“Getting to the conference in Santa Fe isn’t difficult. Someone will drive/fly you there. The hard part is deciding to go. And yet, it might take 8 hours to arrive.
If they invented teleportation and offered it for free, it would be very clear that where we went would simply depend on where we decided to go, not the mechanics, cost or time it took.”
—Seth Godin, At the speed of judgment
Even if we could remove all barriers of travel time, energy, and expense—even if you could snap your fingers and appear there instantly—many people still wouldn’t go.
Why? Because something else matters more.
Here are some obvious reasons people say yes (or no) to a conference:
- Relevance of content
- Potential personal and employer benefits
- Opportunities for meaningful connection
- Location
- Cost
- Time commitment
- Sense of belonging or inclusion
- Physical environment and experience design
- Health and safety considerations
- Employer support
- Timing and life conflicts
- Previous experience or word of mouth
- Opportunities to contribute
- Event marketing effectiveness
But one factor—quiet, powerful, and usually overlooked—can outweigh them all.
Trust.
If I don’t trust the people convening, designing, or running the event—if I don’t believe the experience will be welcoming, thoughtful, and aligned with my values—I’m not going.
If I suspect the event will be rigid, overly hierarchical, sales-driven, or soulless, no travel convenience, discount code, or high-profile keynote will convince me to show up.
And, if I believe I’ll feel like a passive object to be “delivered” content, rather than a human being invited to participate meaningfully, I’ll stay home and read a good book instead.
What kind of trust matters?
Attending a conference requires multiple kinds of trust. We often don’t articulate them, but they quietly shape our decision long before we hit “Register.”
- Do I trust that I’ll be respected—not just tolerated?
If I don’t see people like me in your program, if your language feels exclusive, if your agenda looks like it hasn’t changed in 10 years—I can’t trust that I’ll be seen, and my wants and needs will be met. - Do I trust that my time will be valued?
Will the sessions invite participation, not just absorption? Will the breaks be long enough for real conversation? Will I be treated as a peer, not a lead? - Do I trust that the people there will be open, curious, and generous?
One of the most reliable reasons I choose to attend a conference is because I’ve met someone who’s gone and said, “You’ll love the people there.” - Do I trust that the environment will help me thrive?
This includes the design of the space, the facilitation style, and even the food and seating. Events that center human needs build trust before the first session even begins. - Do I trust the organizers to hold complexity?
In a world full of nuance, competing needs, and uncertainty, I want to be in spaces led by people who don’t pretend everything is simple—or worse, try to sell certainty as a service.
How to build trust?
You don’t build trust with good intentions or glossy branding. Instead, you create it through design, invitation, and experience.
You build it when organizers:
- Engage participants as co-creators, not just attendees
- Tell the truth about what the event is, and what it isn’t.
- Make the invisible visible—by explaining why things are structured the way they are.
- Invite vulnerability and model it themselves.
- Honor differences while creating spaces where people feel like they belong.
When I design and facilitate conferences, I spend just as much time thinking about how to establish trust as I do creating the event process.
Because without trust, nothing meaningful happens.
With it, almost anything can.
So… do I trust you?
That’s the real question every potential attendee is asking, whether they know it or not.
Before they register.
Before they book a flight.
And before they block out three days on their calendar.
They are deciding whether your event feels like a space where they can show up fully, safely, and meaningfully.
You may think you’re organizing a conference.
But you’re actually designing a trustworthy experience.
And the better you do that, the more likely I am to come.



 If people come to meetings to learn, how can we create the best environment for them to do so? It turns out that trust and safety are prerequisites for optimum learning at meetings. Let’s explore why.
If people come to meetings to learn, how can we create the best environment for them to do so? It turns out that trust and safety are prerequisites for optimum learning at meetings. Let’s explore why.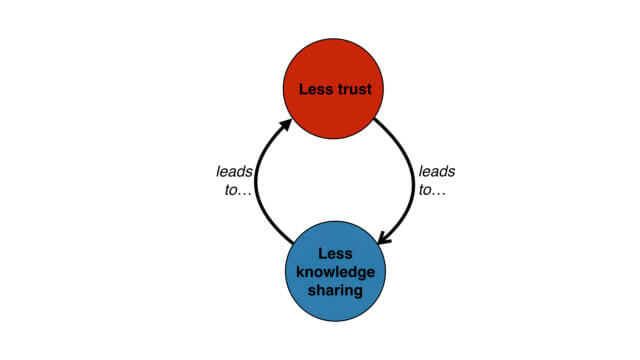
 A shoutout to
A shoutout to 


